Secure your Business Central extension code using a hardware token.
If you develop Business Central extensions, I’m quite sure you’ve published to AppSource. That is unless you exclusively develop on-premise extensions or stay within customer range. Anyways, we’re talking about publicly available extensions.
AppSource is a great platform, it is well-suited for Business Central. Microsoft has done a great job in Dynamics department. It must be very difficult for direct competitors to keep up.
Publishing to AppSource can be a very difficult endeavor, and each one of us have suffered through ever-changing requirements. Not only do you have to write generalized code, comply with localizations, fix bugs and then compile, test, and sign the code. But, this is where I ran into an issue. Of course, I’ve signed the code before, but my certificate had expired, and I went to go get a new one. I thought that I’d just have to go to the place where I’d gotten my last certificate and get a new one. Little did I know, I could no longer just buy my certificate and download it.
Some new standard had been introduced to improve all our lives to make things more secure and safe. Of course, we love safety and will do anything to comply, after all, what choice do we have? I had to go do some research, I found that apparently “Starting in May 2023, new industry requirements from the CA/B Forum require that all code signing certificate keys are stored on an HSM or compliant hardware token.”
What a surprise, I thought that I was going to get my certificate within 30 minutes. Turns out that the most usual form that this hardware token takes shape is as a USB stick. I’m not sure if this USB has any specialized chips or whatnot, but I needed it yesterday. So I decided to go ahead and buy it. It’s worth noting that it used to cost around $99 a year for this Code Signing Certificate, which was an entirely fair price for authenticating yourself and your code. To my surprise, the new price for this more secure way to improve our lives is going to cost me over $300 a year.
What a rip-off, I thought. I almost didn’t want to buy it, but I had to. If didn’t buy it, customers weren’t going to get their improved extension which already had changed their lives. So I processed the order and the fun began, I had to authenticate myself through email, of course, and the certificate issuer had to do some sort of “validation” process. I’m guessing that they checked the validity of our company, D-N-B profile, maybe FEIN, and such.
Outside of being overly concerned with this new process and price, my urgency to get my certificate lead me to call customer service and ask them if I was doing everything correctly and if there is anything I could do to expedite the process. Few things were remaining, and one of those things was a requirement to send in a selfie while holding an ID. Yes, they wanted a picture of me while holding my driver’s license. What a genius way to issue a certificate, they would know what I look like if my code ends up somewhere at the wrong place at the wrong time.
I would be found in no time. So, I took my driver’s license and phone, positioned myself into the front facing camera and snapped a picture, and uploaded it to my account. Turns out the driver’s license wasn’t readable, it was too blurry to be acceptable to issue a code signing certificate. What could I do other than take another picture, which I did, and it was now acceptable.
Now I just needed to wait for the USB and I couldn’t help but imagine the difference between now and then. Just a short year ago, I was able to get my certificate near instantaneously. Now it has to be shipped to me, and before it does I have to jump through many different hoops, which seems entirely unnecessary to me. Anyways, a day or two later I got an email saying that my certificate was in the mail. In the meantime, we had customers waiting to get an important update. We had fixed a few bugs and added features, and now we were ready to publish, but we didn’t realize that our certificate had expired. Yes, I had missed the date, it was there on the calendar, and I had ignored it, I thought, “I will do it when I get a few minutes,” after all it would only take few minutes out of my day.
This code signing certificate, while being the exact same certificate, is a whole new process and I’m sure it’s great and secure, but now I can’t just download or generate a pfx file, share it with my developer colleagues and sign away. I will have one USB and if my colleagues are in different countries, there wouldn’t be a convenient way to get the USB to them. This means that we’ll all have to share one USB, so perhaps we could plug it into a server and sign our apps from that server. Perhaps, we’ll see when I get it. In the meantime, I had a 3-week vacation coming up, and the USB would arrive a few days after I left. So, I told my colleagues at the office that the new certificate is coming in the mail.
It took a while to receive the certificate, and when I got notified that it’s here, I immediately asked my colleague to turn on my computer at my desk and insert the USB. I could access my computer remotely since it was on GoToAssist. Very convenient while you’re away on vacation, and a great way to access client’s computers or your own.
The only way to access my certificate was to install a utility software onto my computer. This utility is luckily documented on the certificate issuer’s website and was a no brainer to install. I had never ever dealt with hardware keys, so this procedure was all new to me. “How do I generate my pfx file now?” I thought. The utility showed me the certificate, I saw it, and it looked like a version of Certificate Manager on my computer, but within this utility and only one certificate is there.
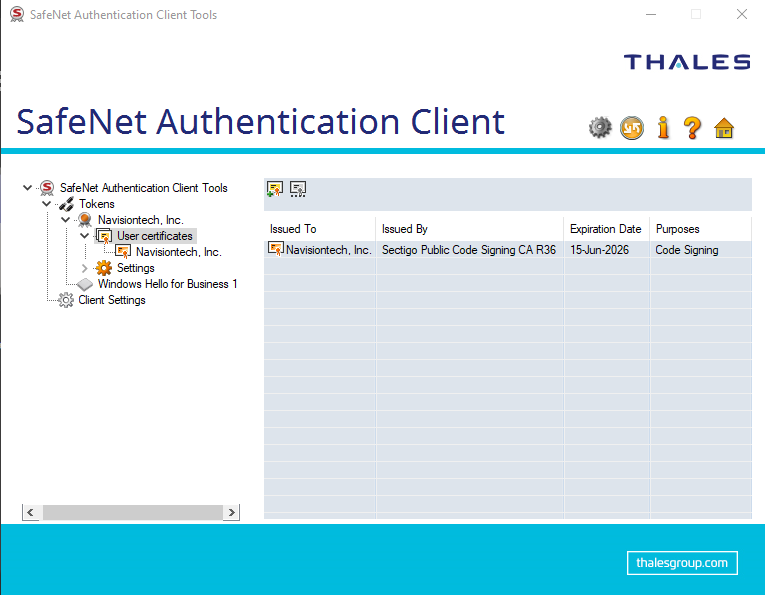






I’m having a similar problem, only that the bought key is now in azure key vault and all ic asn download from it is the pem file. Problem is I don’t understand Microsofts instruction on using the azure key vault for signing my code. It’s annoying af!
Microsoft’s instructions on this topic are outdated, at least at the time when we had to deal with this. Azure Key Valut sounds like another annoying adventure.
Thanks a bunch ! This worked for me !
Glad we were able to help!
I am facing the same issue and could not get my app file signed, in your blog you had mentioned “:\path\to\fileToSign.exe” but the BC app file extension is .app. Is there something I am not following could you share some more info on this.
Anwar, the example states .exe for sample purposes only. You are right, you do need to use .app extension. The command is executed from “C:\Program Files (x86)\Windows Kits\10\App Certification Kit” and should be
"signtool sign /sha1 [your cert hash] /tr http://timestamp.sectigo.com /td sha256 /fd sha256 /n ["Org Name"] ["full_path_to_file.app"]Hope this helps.
Hi gvol, Thanks so much for your reply.
I still get the error, here is the command I am executing with Admin privileges
PS C:\Program Files (x86)\Windows Kits\10\App Certification Kit> .\signtool sign /sha1 xxxxx00000 /tr http://timestamp.sectigo.com /td sha256 /fd sha256 /n “My Company” C:\Users\Tech1\Desktop\cert\App1004.app
Done Adding Additional Store
SignTool Error: This file format cannot be signed because it is not recognized.
SignTool Error: An error occurred while attempting to sign: C:\Users\Tech1\Desktop\cert\App1004.app
Do you think, anything needs to be done in the signtool.exe.manifest.
I have downloaded and installed the Windows Kit, but the error persists.
I appreciate your help and reply.
Regards,
Anwar
That happened to me as well, this means you dont have Business Central installed on your machine. You need some version of Business Central installed. This said, i dont think you can sign on mac even though singtool equivalent exists in macOS. If anyone knows otherwise, please let us know.
Hello , I need help, I am familiar with signing the app file, but the certificate was given by my IT team, but right now in my new company I have to buy it , so can you please guide me from where can i buy this pendrive?
Are you located in US or somewhere else? Let me know and i will send you a link to the right certficate configuration.
Thank you so much for the reply , I am located in Ontario, Canada.
You will want to go here and purchase the Sectigo Code Signing Certificates, pricewise the best option is 3 Years, but you can just get 1 year and then renew, i chose 3 years because i dont want to deal with it for a while.
Oh okay, got it , thank you so much for the information, and one last suggestion I want is that which delivery option is best?
Token + Your preferred shipping method is the best option. If you are outside of the US, simply select International Non-US. i woudlnt go with Installing on Existing HSM unless you already have a token, and even then its worth having this token on its own USB stick.
Hello, this is a very interesting topic. In your opinion, which method is better for signing a BC app: Azure Key Vault or a hardware token, considering both price and efficiency?
When considering efficiency, it’s important to remember that the step of signing an app is critical and should be assigned to a single individual. This person is ultimately responsible for publishing the app and will most likely conduct a code review before doing so. With a physical key requirement, only the individual holding the key can sign the app. While Azure Key Vault also requires authentication, the physical aspect of a key adds an extra layer of security and ensures a more systematic process, in my opinion. Personally, I appreciate that using a physical key forces me to perform a code review before publishing.
However, if you are the sole developer, tester, and publisher of the app, this systematic approach might not make a noticeable difference. In that case, the distinctions between using Azure Key Vault and a physical key may not be significant from a cost or efficiency perspective.